How Hackers Use Hidden Data on Airline Boarding Passes to Hack Flights
Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.
The average airline boarding pass contains a wealth of information that a hacker could potentially take advantage of in two primary ways. How they take advantage of it mostly depends on whether the target has a frequent-flyer account or not.
Airlines have two types of accounts. One is temporary and is created when you buy a ticket that isn't affiliated with an airline miles program, such as when you use Google Flights or Expedia. The other type is a permanent account, which often comes in the form of a frequent-flyer program.
You might think that just not having a frequent-flyer account could keep you from being compromised, but when you don't, your miles are up for grabs. Hackers can use information gleaned from any boarding passes not connected with a frequent-flyer program to go to the airline's website and claim the victim's miles for themselves. By walking through an airport and photographing boarding passes, an attacker could earn thousands upon thousands of rewards miles, which can be used for free flights and upgrades to a paid flight.
Those passengers that do have frequent-flyer accounts could have their accounts compromised. Access to these accounts could give the attacker the ability to view passport information, change passwords, and even cancel future flights.
With the temporary account, an attacker could only cancel the fight or legs of the trip that are on the boarding pass that was scanned. With access to the frequent-flyer account, they can cancel other flights that are months away and not associated with the current trip.
We'll be looking at how a hacker would acquire a target's boarding information.
Step 1Find a Boarding Pass
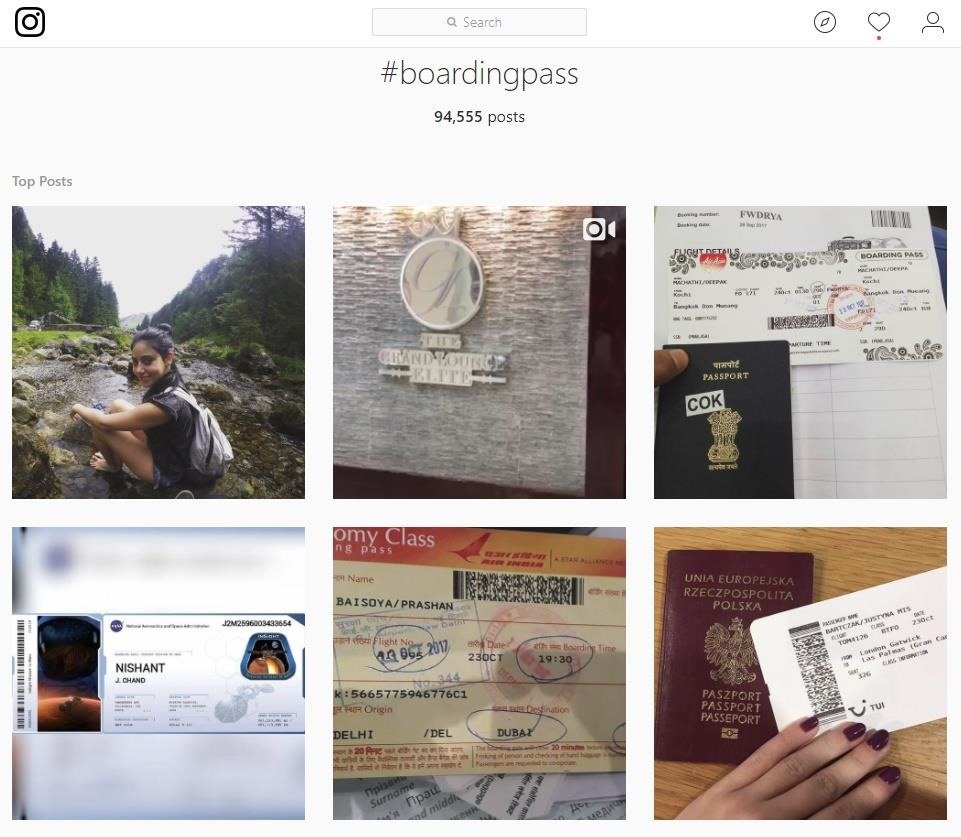
The first step is finding a boarding pass to scan. Specifically, the hacker needs a clear image of a PDF417 barcode on a boarding pass to scan it and capture the information on it. You might think you need to head to an airport to find some boarding passes, but in reality, social media is full of them.
Method 1Use Social Media
Head to Instagram and search #boardingpass to find a plethora of images. When I conducted my search, it yielded approximately 95K results. Obviously, not every single one of those is going to be a scannable boarding pass, and some will contain boarding passes that aren't all that scannable or readable because they are at odd angles or blurry.
It's mind-boggling the amount of personal information this represents encoded in boarding passes and how blasé people are about sharing it.
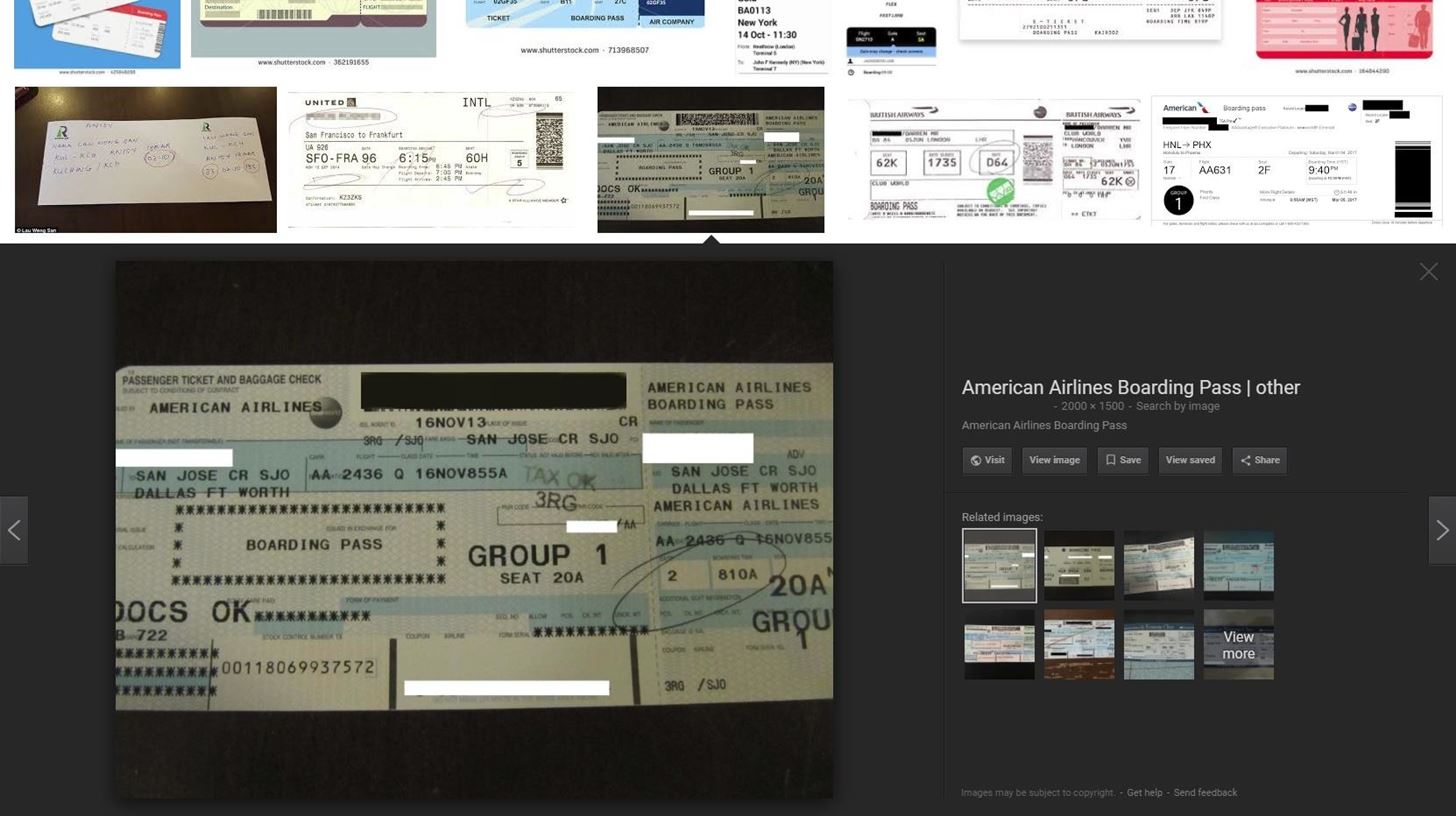
Method 2Use Google Images
Another amazing resource is Google image search. Below, you can see the image of a boarding pass that I found during my search where the photographer attempted to obfuscate what they deemed important information. However, they left the barcode revealed, which I blacked out before posting the image below. The rest of the results are low enough resolution as to be unscannable.
Using that barcode, I was able to reveal all of the information the photographer had attempted to obscure, plus even more information that isn't on the pass in plain text. This demonstrates people's misunderstanding of how a boarding pass fundamentally works and is the reason I'm writing this article.
Out in the real world, a bounty of codes can be found at an airport. Methods for finding them range from techniques that are very suspicious to methods indistinguishable from normal airport behavior.
Method 3Find It in Real Life
The first and least suspicious tactic would simply be walking around the airport recording video. A high-quality video camera or DSLR — or even a modern smartphone — can record in HD without standing out. A hacker could walk around the airport recording, capturing people with boarding passes in hand waiting to board or just outside TSA screening. Once done, the hacker could search the video frame by frame for boarding pass QR codes — a process that could grow tedious.
A hacker could employ social engineering to come up with a reason to take pictures of people's boarding passes. Perhaps they could pretend to be a videographer wanting to make a time-lapse of the flight attendant scanning all the boarding passes or a photographer doing a portrait series of various families and where they're traveling to. Either way, this is naturally more suspicious than the passive video technique, yet could potentially be more useful if the hacker was attempting a targeted attack on the particular individual or wanted a less tedious approach than scanning videos.
The most suspicious tactic would be to attempt to come into physical possession of the boarding pass by digging through trash cans or asking people for their old boarding passes after a flight. That's pretty unnecessary, though, since all they need is the image of the barcode, not the actual pass.
Step 2Scan the Boarding Pass Barcode
There are two ways a hacker can scan a boarding pass. The first is to use a free mobile application on a smartphone, while the second uses a web-based tool to accomplish the same function. While I'll teach you to use both, the web-based interface has more functionality and tends to work better.
Method 1Use a Mobile Application
Once someone has a clear image of your boarding pass barcode, it's a simple matter to scan it. There are a variety of ways to approach this. Of course, if you wanted to get into the nitty-gritty code side of scanning barcodes, a good place to get started would be BarcodeSanner on GitHub. It could be implemented into a program that scans video for these barcodes, such as in the example we discussed above.
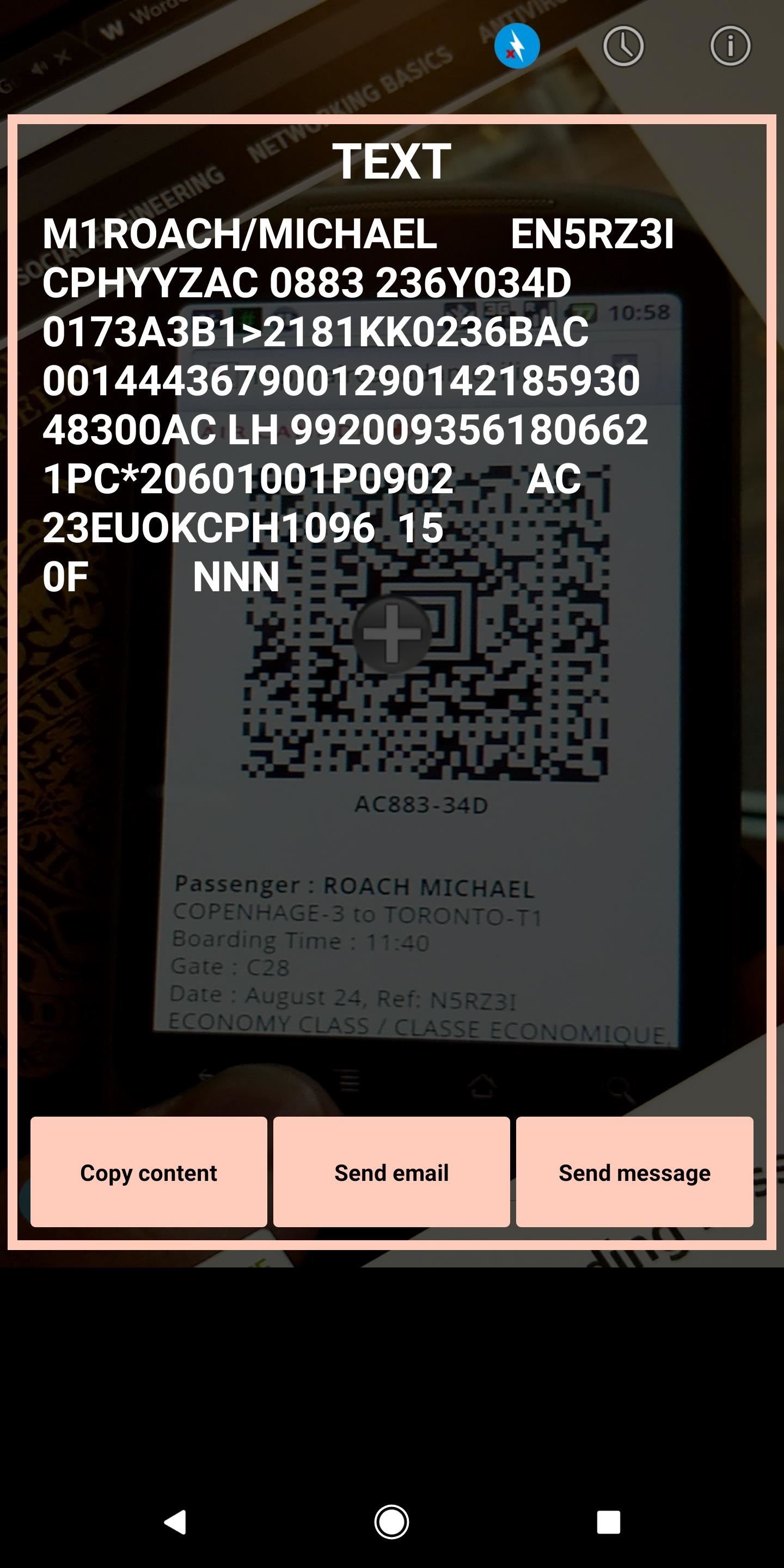
With physical access to the boarding pass, any number of free QR and barcode scanner apps from the Google Play Store or iOS App Store make it super simple to scan barcodes. For our example, we used Lightning QRcode Scanner. Open the app, and then give it permission to use your camera. Point the phone at the barcode on the boarding pass to scan the barcode. The app will spit out a long string of formatted text, looking something like the image below.
Method 2Use a Web Tool
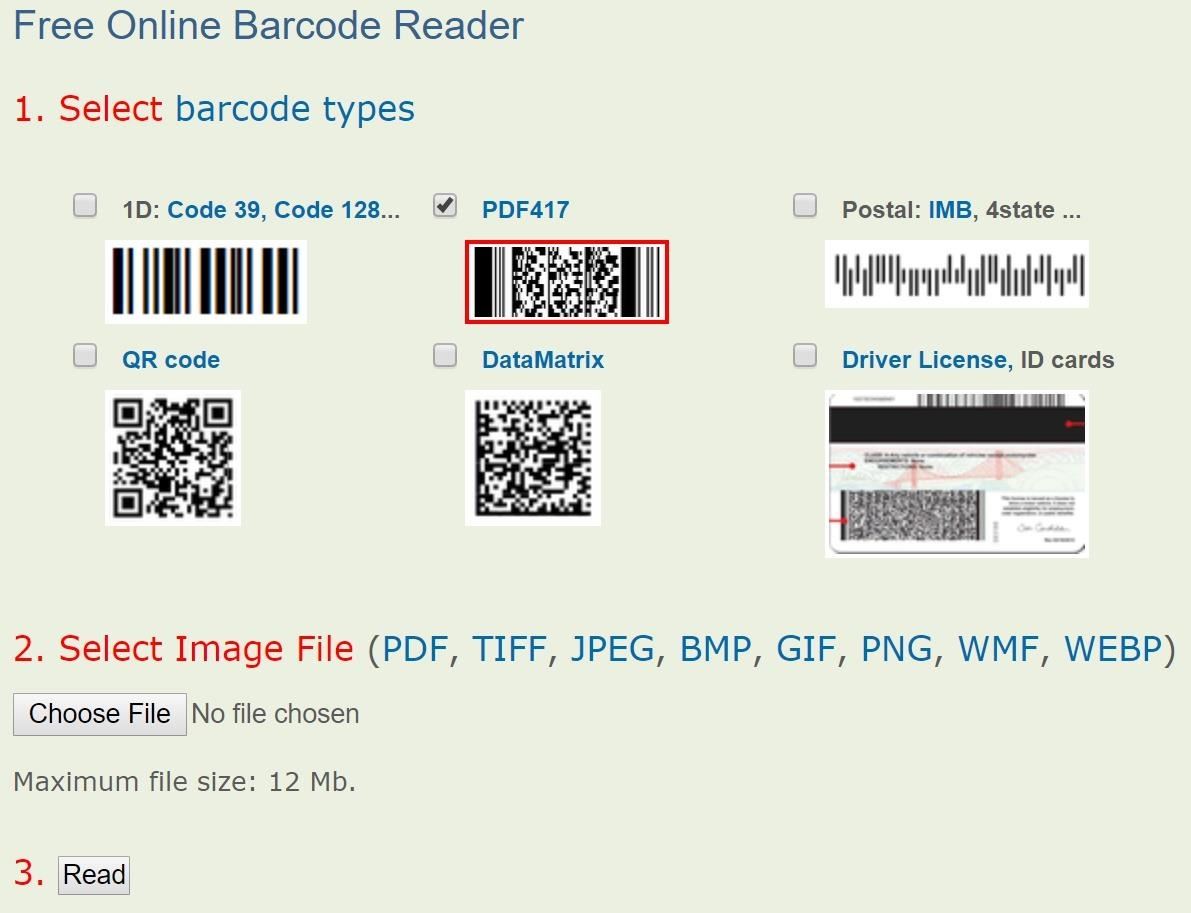
Additionally, a web tool such as Free Online Barcode Reader by Inlite can be used. It would most likely be used if the hacker were doing the internet scavenging technique we first talked about. They would only need to download the image, then re-upload it to the website to see the encoded data.
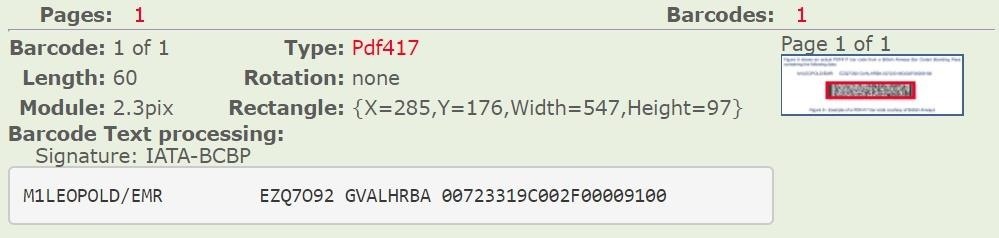
Upon a successful scan, a string of data should appear. At first, this might look like gibberish. What does "M1LEOPOLD/EMR EZQ7o92 GVALHRBA 00723319C002F00009100" even mean? In the next step, we will look at how precisely this can be decoded to glean valuable information.
Because the Inlite tool is the only one that I know every reader will have access to, let's quickly cover how to use it. Begin by selecting the barcode type. That is most likely going to be PDF417 in the case of a physical boarding pass or QR code if it's from a smartphone.
The web tool allows you to select multiple types simultaneously. After that, click "Choose File" and select the image. Make sure it's in one of the acceptable formats. Most cameras use JPEG, so they should be fine for this. Lastly, click "Read" to attempt to read the selected barcode.
Below is what a successful read looks like. This tool is quite good and has worked on some images that other apps struggled with.
Step 3Decode the Boarding Pass
The International Air Transport Association (IATA) is the international body that creates guidelines and standardization for the airline industry. Naturally, they're the ones that created the current boarding pass standardization (Bar Coded Boarding Pass Implementation Guide) that hackers can take advantage of.
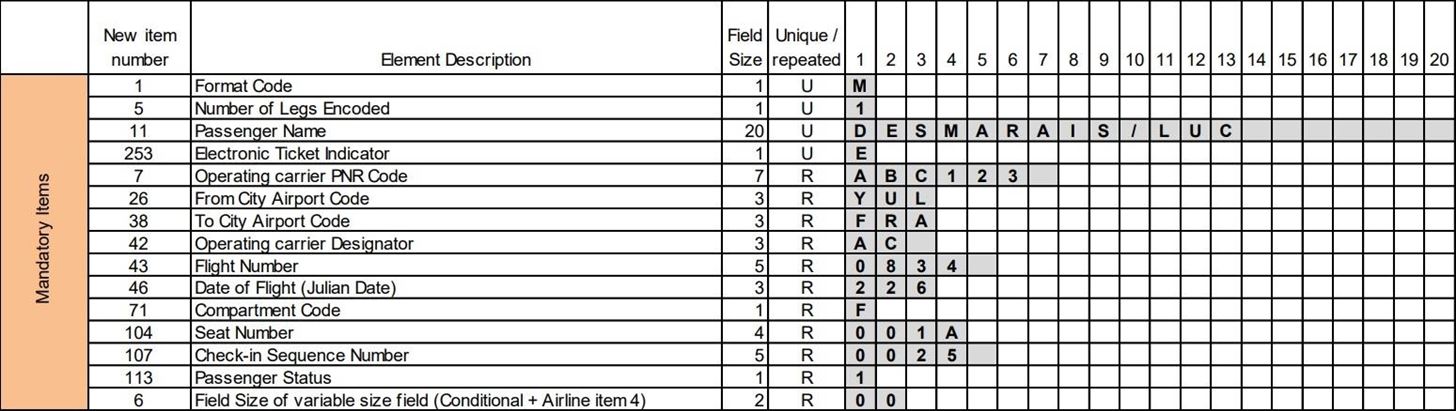
The guide below denotes what each character in the string of data contained within the barcode means. There is quite a lot of information that can potentially be stored in the 30 fields. However, the most interesting to us is the first block, the mandatory items, as this contains all of the identifying information such as passenger name and flight information.
If you look closely at the mandatory items, you'll notice that there's no integrity check on the data required. That means there is no way to check if the information has been changed since it was printed. As if that wasn't bad enough, the authentication for the boarding pass is not listed as a mandatory item, which means this is commonly not used and also represents a gaping security flaw. In practical terms, this means an attacker could essentially insert false information into the data string, generate a new barcode, and still have a valid boarding pass. We'll look at this in greater detail in a future article.
Now, let's take an example of a British Airways flight and see what information we can parse from it. Let's use that string of gibberish from before.
M1LEOPOLD/EMR EZQ7o92 GVALHRBA
Looking at the chart above, we can see the field size allocated for each element. The first two are a single character each, which tells us that the form code is "M" and the flight is "1" leg. After that, there is room for a last and first name 19 characters in length. It would be 20, but one is used for a backslash separating the first and last name. If the first and last name exceeds 19 characters in length, it's truncated to save space.
Here you can see the name is Emr Leopold. Following that is "EZQ7092", which is the passenger name record (PNR) code, also referred to as the booking reference. This is one of the most valuable pieces of information on the boarding pass.
This PNR code is a temporary password used often in conjunction with the passenger's last name, but this can vary from airline to airline. Because of way code-sharing agreements between airlines work, this PNR code can be used to gain access to a target's frequent-flyer account, which we will look at in the next step.
After the PNR code is the departing and arriving airport, followed by the air carrier. In this example, we have "GVALHRBA" which would translate as Geneva (GVA) to London Heathrow (LHR) via British Airways (BA). Each of these codes is easy to search for on Google if you don't already know them. A full list of all the airport codes is also publically available.
In a real-world boarding pass, there would be substantially more information for us to read. As you can imagine, it would become very tedious to parse it all by hand, which is why a hacker would likely make a simple Python script to do so, such as the IATA-Parser on GitHub.
Step 4Gain Access to a Target's Account
The last step for a hacker is to input the data on an airlines website to log into the user's account. The precise steps vary from airline to airline, but the general technique is the same.
For example, looking at the pass we just decoded, the hacker would go to the British Airways website. There they would navigate to "Manage My Booking" and input the PNR "EZQ7092" as the booking reference and "Leopold" for the name. Then they would have access to the temporary account with all the same power to make changes as the legitimate owner.
How to Defend Your Boarding Pass Data
There are a number of simple steps you can take to protect your boarding pass and the information it contains. The first thing you can do, if you are fairly confident in the security of your smartphone, is check in online and use your smartphone as your boarding pass. This prevents anyone from seeing the physical boarding pass, as you don't have one, although you will still need to protect the scannable code.
If you do need to carry around a physical boarding pass, be sure to keep it tucked away when not in use. Additionally, fold it with the back facing out so that the barcode can't be readily seen. Lastly, don't ever throw your boarding passes in the trash. They should be safely disposed of by shredding.
It goes almost without saying, never post photos of your boarding passes online and most definitely don't tag them as such. This is particularly true before a flight, as an attacker could cancel your flight without you knowing.
Most of the information a boarding pass contains within the barcode is harmless when taken by itself. However, when one takes into account that this information can be used to gain access to airline accounts, it becomes much more dangerous. While it's unlikely that a random hacker would go around canceling your future flights, it's never a good idea to leave your boarding pass security up to the goodwill of hackers.
A more likely threat is a hacker going around claiming unclaimed miles, so remember to sign up for your frequent-flyer programs to prevent this. While doing so, be careful what information you give out, just in case your account is compromised.
If you found this interesting, Przemek Jaroszewski reviewed some new tools that make hacking boarding passes easier than ever at Defcon 24 in August of 2016. You can check out the Defcon talk below if you have an hour free to watch. I highly recommend it. He discusses how the boarding pass information is created, encoded, and validated, then explains how easy it is to craft your own boarding pass.


Comments