Detect Misconfigurations in 'Anonymous' Dark Web Sites with OnionScan
Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.
As security researcher @x0rz demonstrated in an article on securing onion services, websites are often de-anonymized all too easily. He utilized software such as cURL, a command-line tool used for transferring data using various protocols, to collect HTTP response headers for later Shodan queries.
All of the methods x0rz used to de-anonymize the onion services should have been ineffective if basic safeguards were taken by the site owners. System administrators need to take better precautions to prevent their websites from being vulnerable to server fingerprinting and enumeration. And that's where OnionScan comes into play.
What Is OnionScan?
OnionScan is a free and open-source tool designed for investigating onion services. Its written in Go, a programming language created by Google in 2009. OnionScan's primary goal is to help operators of onion services identify and fix operational security (OPSEC) issues with their services. OnionScan can also be used to help researchers and investigators monitor and track sites on the dark web.
The developers of OnionScan aim to make finding vulnerabilities as simple as possible. Not because they agree with the motives of every investigation force in the world, but because they believe that by making these kinds of audits easy, they will create a powerful incentive for new and improved anonymity technologies.
Step 1Installing OnionScan
Let's dive in and take a look at how to run OnionScan on a Kali box. You can run this in a virtual machine, on a laptop, or on a Raspberry Pi. Before starting, make sure your system is up to date by typing apt-get update into a terminal window.
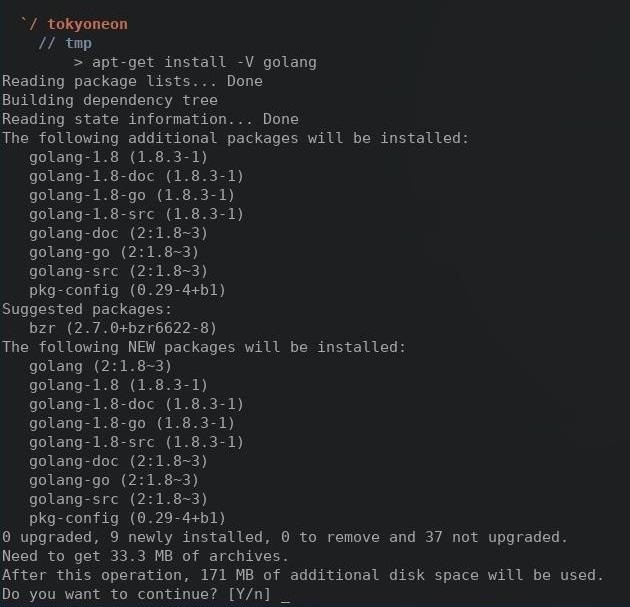
Then, let's make sure we have Go installed. This dependency is required to install OnionScan, so open a terminal and type the following.
sudo apt-get install golang
When that's done installing, we'll need to clone the OnionScan repository from the developer's GitHub page. In the same terminal window, type the following.
go get github.com/s-rah/onionscan
Then compile it by running this command:
go install github.com/s-rah/onionscan
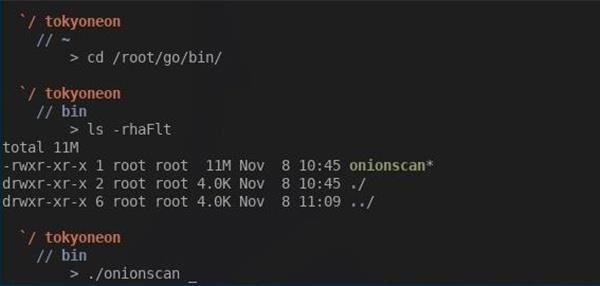
Change into the /root/go/bin directory to by typing cd /root/go/bin into the terminal. Then list the directory contents with ls.
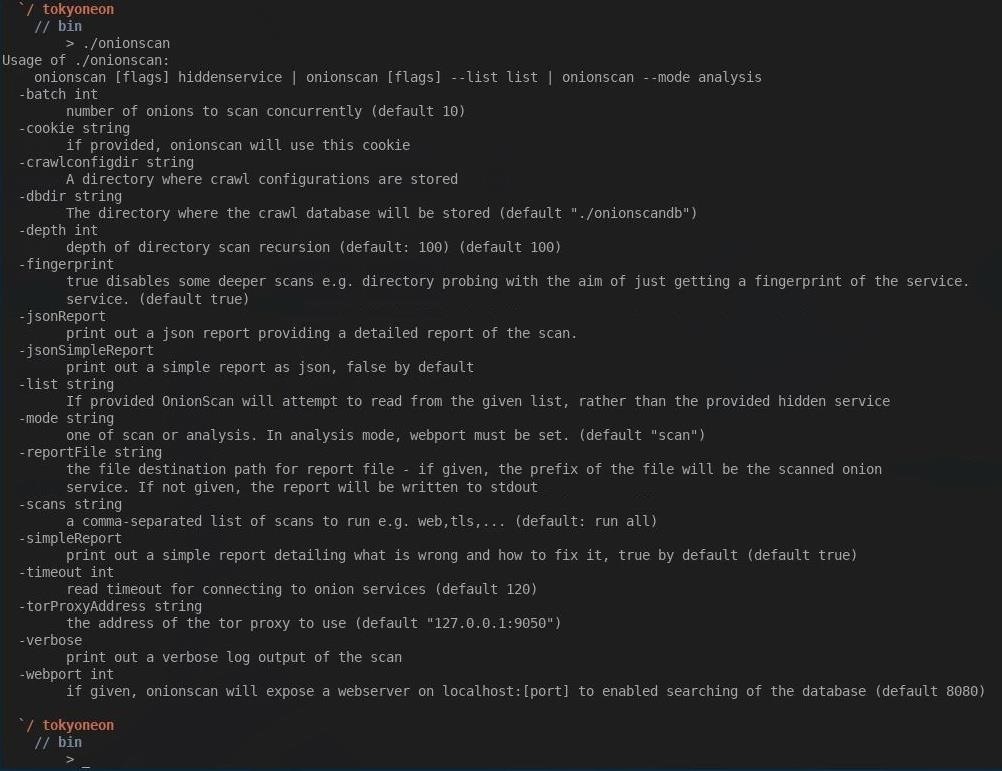
That's it for installing OnionScan. Simply executing ./onionscan from the /root/go/bindirectory will invoke the help page and provide all the available options.
Step 2Using OnionScan
For this demo, I'll be anonymizing my Kali box with Whonix. Doing this will route all of my network traffic through the Tor network. To do this, you can refer to our tutorial linked below.
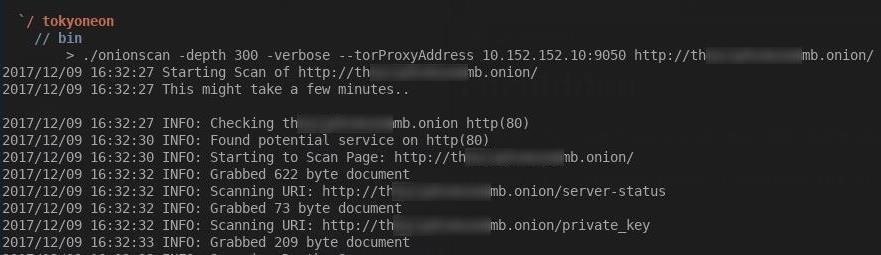
This is primarily for convenience, as OnionScan only works against onion sites. To use OnionScan, type the command below into a terminal window.
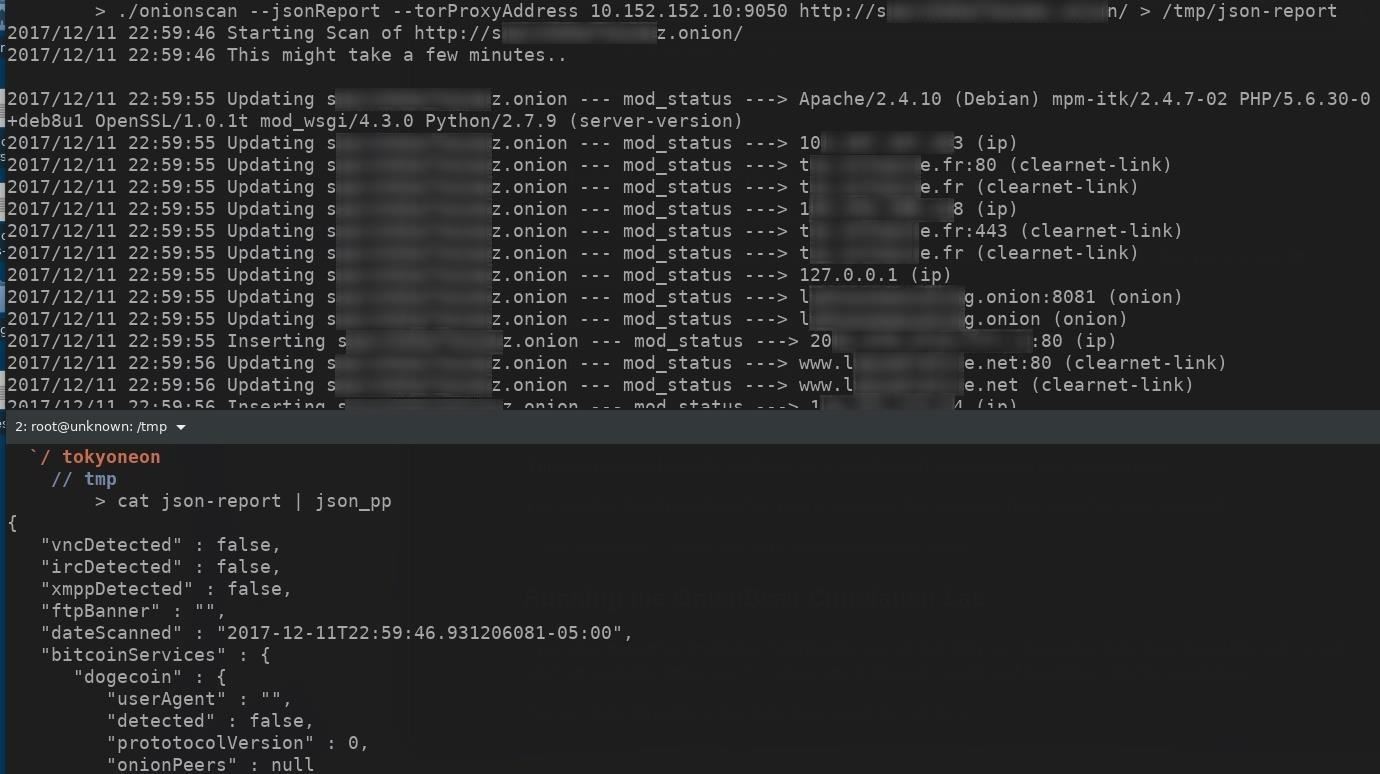
./onionscan --torProxyAddress=10.152.152.10:9050 youronionservice.onion
The --torProxyAddress part tells OnionScan to use a proxy, while 10.152.152.10:9050 is a Tor proxy port in the Whonix gateway. This argument will tell OnionScan to proxy requests through the Whonix gateway.
For non-Whonix setups, we would use 127.0.0.1:9050 as our torProxyAddress.
./onionscan --torProxyAddress=127.0.0.1:9050 youronionservice.onion
OnionScan also offers an alternate JSON output format for integration with other applications like Censys and programming languages such as Python and JavaScript.
./onionscan --torProxyAddress=10.152.152.10:9050 --jsonReport youronionservice.onion > /path/to/save/destination/filename.json
Step 3Protecting Yourself & Your Onion Services
Did OnionScan report a "High Risk" vulnerability with your onion service? Don't be alarmed. There are steps we can take to resolve these issues. Below, I'll cover how to fix and prevent some of the most common vulnerabilities discovered by OnionScan.
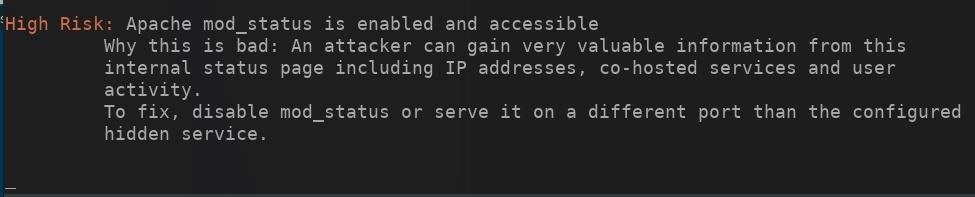
1Apache mod_status Leak
The Apache status module allows a server admin to actively monitor how well their server is performing. An HTML page is presented that provides the current server statistics in an easily readable form. With this information, attackers can:
- Build a fingerprint of your server, including version information for PHP and other software.
- Determine client IP addresses if you are co-hosting a clearnet site.
- Determine your IP address if your setup allows.
- Determine other sites you are co-hosting.
- Determine how active your site is.
- Find secret or hidden areas of your site.
By default, this module is enabled and accessed by appending /server-status to the website URL. This is still one of the biggest issues we find with dark web sites today.
How to Fix This
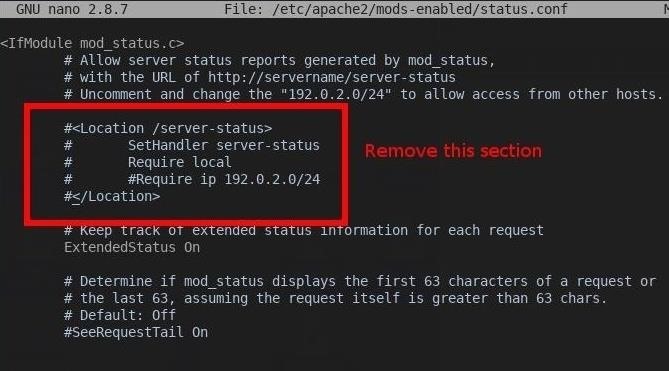
Comment out or completely remove the <Location /server-status> brackets in the status.conf file. Open a terminal and type the command below to access it.
nano /etc/apache2/mods-enabled/status.conf
After modifying the status.conf and saving the configuration, restart Apache by typing the command below into a terminal.
sudo apachectl restart
You'll notice visiting http://youronionservice.onion/server-status now returns HTTP status code 404. This means you've successfully disabled mod_status.
2Open Directories
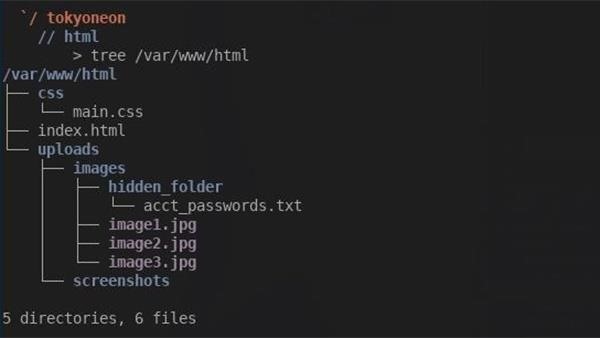
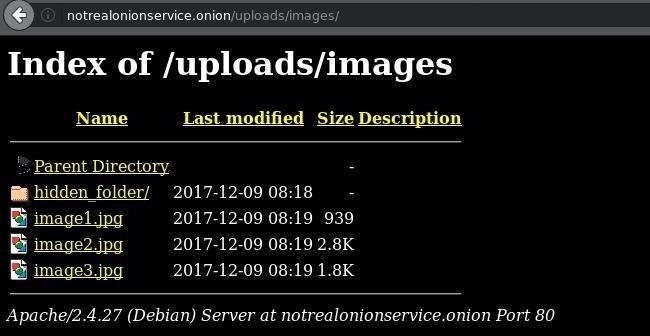
By default, appending a trailing slash to a URL will instruct Apache to return the contents of a given directory. For example, I added a /hidden_folder/ to my website. The image below shows the directory structure of my website.
In the /images directory, we can see the hidden_folder, which would not normally be discovered by an attacker. With directories openly accessible, visiting http://youronionservice.onion/uploads/images/ will disclose the contents of the entire directory. The image below is an example of that.
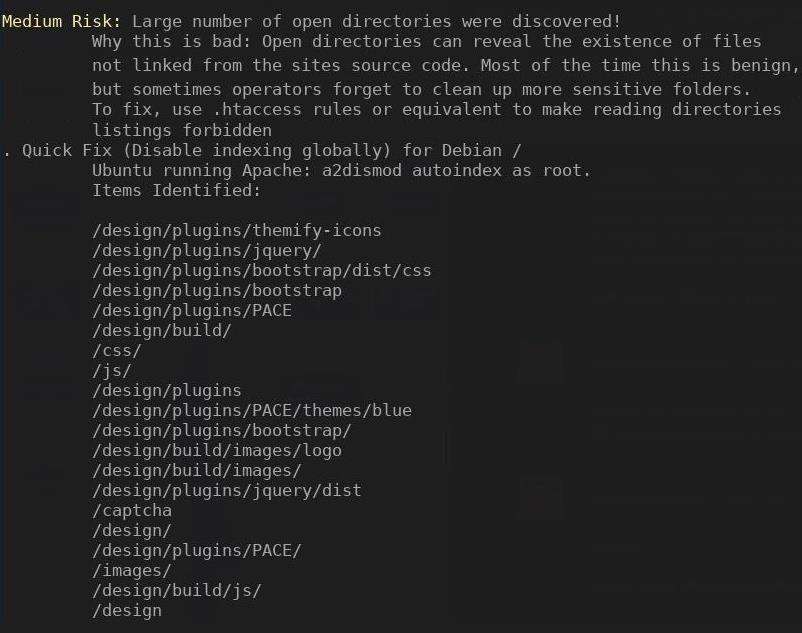
OnionScan will list every directory it was able to access. The image below is an example of OnionScan reporting open directories.
How to Fix This
We'll need to modify the apache2.conf. Open a terminal and type the following command.
nano /etc/apache2/apache2.conf
Find the <Directory /var/www/> brackets. Notice the Indexes between Options and FollowSymLinks. Here is how the brackets look by default:
<Directory /var/www/>
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
</Directory>
Remove Indexes entirely, and it should look like this when we're done:
<Directory /var/www/>
Options FollowSymLinks
AllowOverride None
Require all granted
</Directory>
Save and close the file, then restart Apache by typing the following command into a terminal.
sudo apachectl restart
3EXIF Tags
EXIF stands for Exchangeable Image File and is stored in JPEG, PNG, and PDF file types. This embedded data can sometimes reveal interesting information, including timestamps, device information, and GPS coordinates. Most websites still do not properly sanitize EXIF data from images, leaving themselves or their users at risk of de-anonymization.
A perfect example of the dangers of EXIF data is the arrest of Higinio Ochoa. FBI agents extrapolated his girlfriend's geographic location using the GPS data found in a photo Higinio uploaded to Twitter.
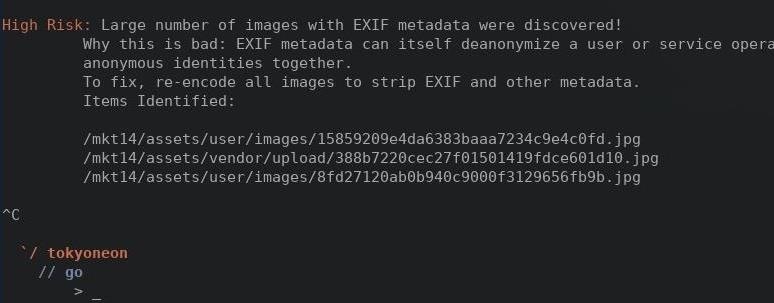
OnionScan will list every photo which may contain sensitive EXIF metadata. The following screenshot is an example of OnionScan reporting harmful EXIF metadata discovered in JPGs found on an onion website.
How to Fix This
We need to manually remove EXIF metadata from our images. Below are several recommended metadata wiping tools.
- ExifTool, a Perl application for editing metadata in a wide variety of files.
- Exiv2, a C++ application to manage image metadata.
- Jhead, a JPEG header manipulation tool.
- Pdfparanoia, a tool to remove watermark from academic papers.
I'll be using MAT (Metadata Anonymization Toolkit), a command-line tool used to remove metadata from images, which can be found in most popular Linuxdistribution repositories. To install MAT, open a terminal and type the command below.
sudo apt-get install mat
After MAT is installed, we can display harmful EXIF metadata by typing the following command into a terminal.
mat -d image.jpg
The -d will instruct MAT to list all harmful metadata of a file without removing it. This is useful for viewing EXIF metadata without wiping it. To completely remove all the EXIF metadata, type the following command.
mat image.jpg
4SSH, FTP & SMTP
OnionScan collects SSH public key fingerprints, SMTP banners, and other FTP, IRC, Ricochet, and MongoDB server information. These banners are often misconfigured to reveal information about the target server, including OS versions, hostnames, and IP addresses. This information can be compared to other onion and clearnet servers in order to try and identify the actual server location.
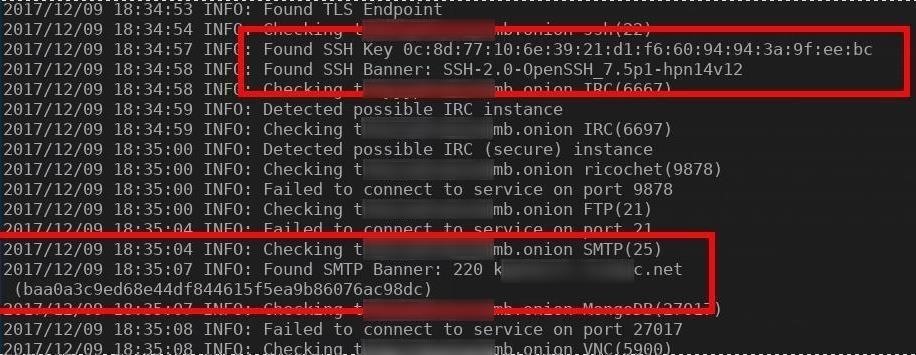
This image is an example of OnionScan revealing SSH and SMTP banners:
How to Fix This
By default, SSH will try to listen on 0.0.0.0. This means your SSH server will attempt to broadcast on every interface, making your SSH server accessible to search engines like Shodan. Modify the SSH config file by typing the following command into a terminal.
nano /etc/ssh/sshd_config
Notice the "ListenAddress" line is set to 0.0.0.0.
ListenAddress 0.0.0.0
ListenAddress ::
We'll need to modify that to 127.0.0.1 so it looks like the following text.
ListenAddress 127.0.0.1
#ListenAddress 0.0.0.0
#ListenAddress ::
Save and close the sshd_config file, then restart your SSH server by typing the following command into a terminal.
sudo systemctl restart ssh
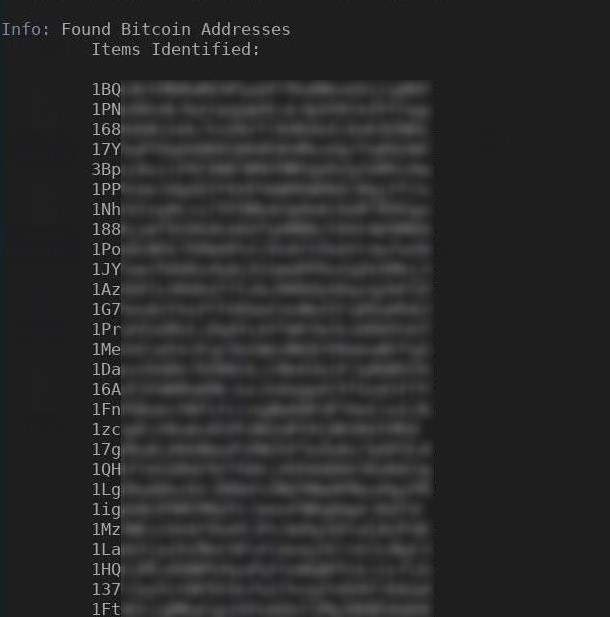
5Cryptocurrency Clients
OnionScan scans for common cryptocurrency clients including Bitcoin and Litecoin. From these, it extracts other connected onion services as well as the user agent.
How to Fix This
If it's not absolutely necessary, don't publicly share currency information on your websites. Unfortunately, there's not much we can do to "fix" website scanners and crawlers from collecting your cryptocurrency addresses.
Looking Deeper into the Dark Web
OnionScan is a powerful tool. The image below is a graphical representation the developers created using OnionScan which depicts connections made between a vast majority of sites on the dark web. These connections were established using Bitcoin addresses, Apache mod_status leaks, SSH fingerprints, and other types of identifiers.
While many people may think dark web sites are anonymous by design, the reality is that they require attention like any other site to truly protect the identity of the administrator. Here, we've covered the common ways the owner of an onion service can improve their security, as the most useful methods for de-anonymizing a poorly configured onion service.

Comments